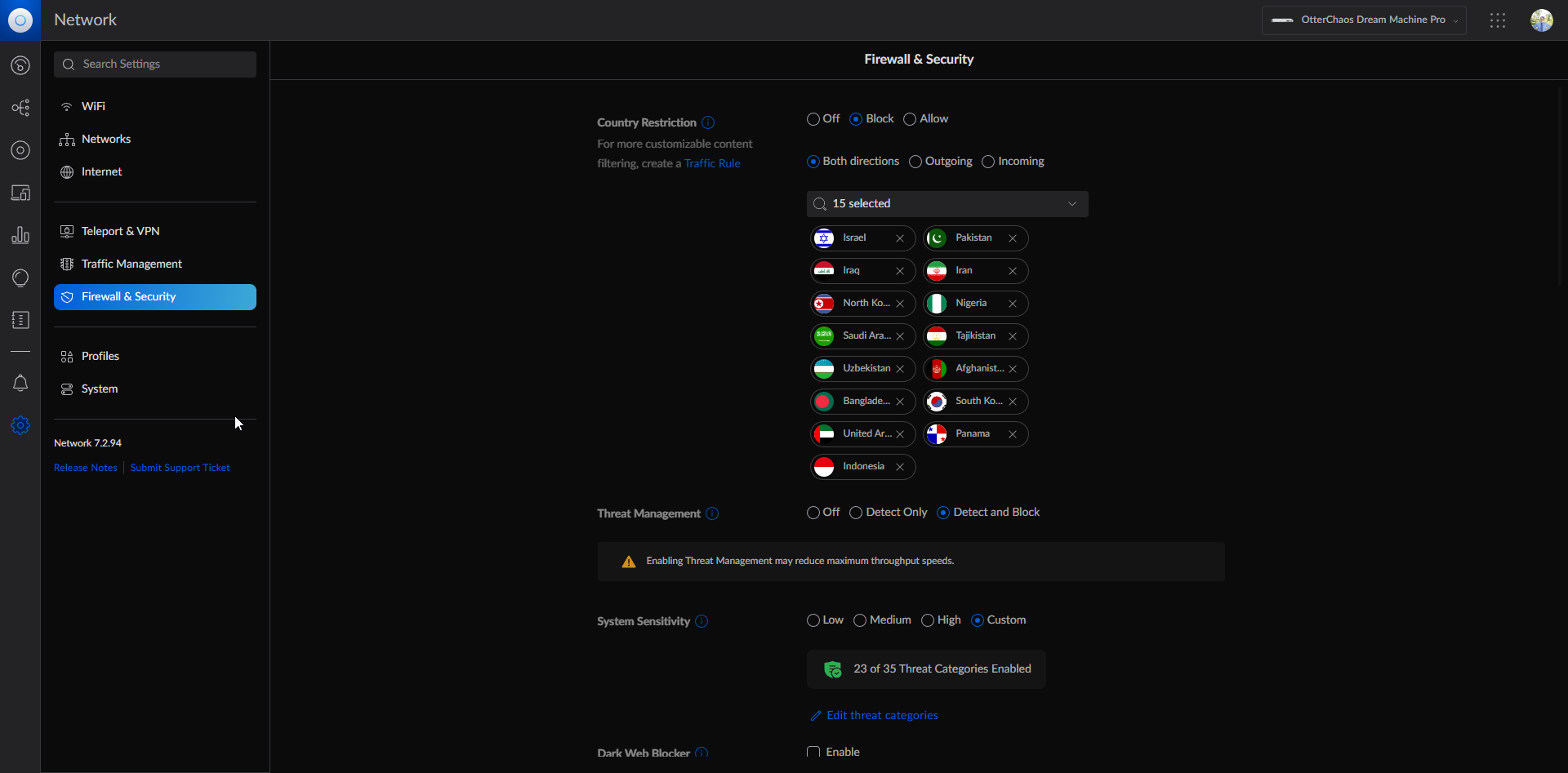
Let's talk security 🛡
Typically, most homelabbers setup their inbound-outbound traffic infrastructure like this:
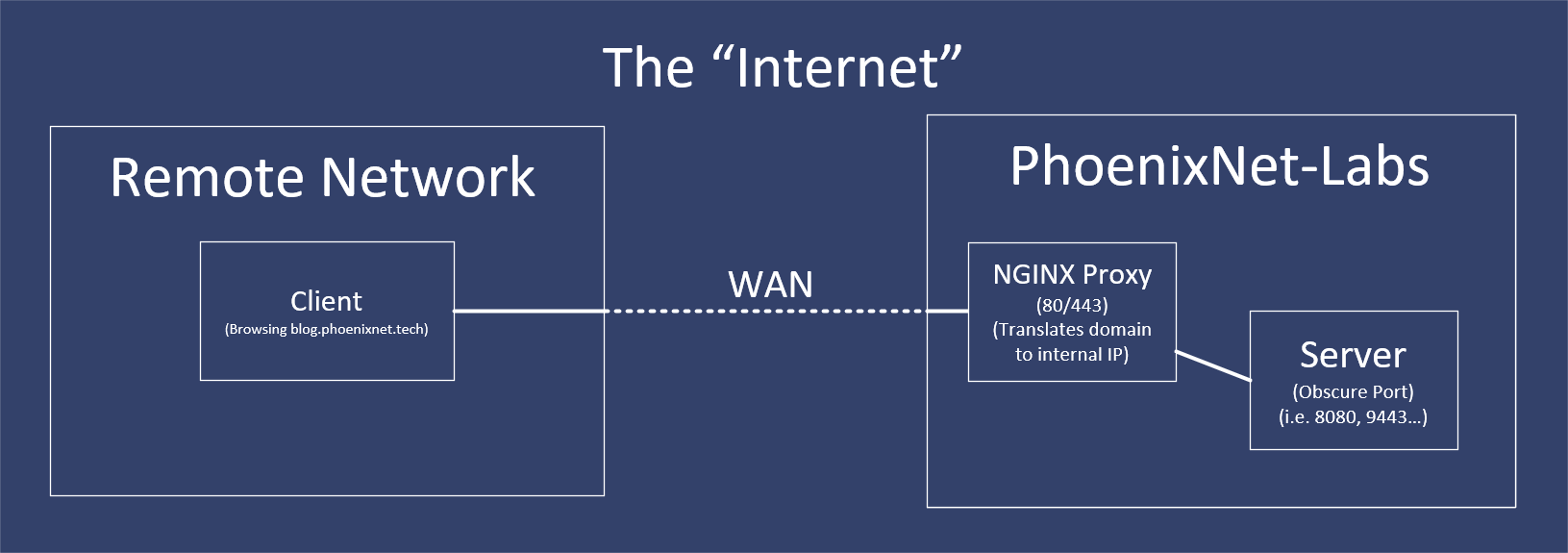
This introduces a few issues:
A) The public IP address behind our intranet is exposed if additional proxies aren't being used. (In this case, they weren't)
B) By exposing my public IP address, I was also exposing my intranet to the possibility of network scans, attacks, and intrusion.
C) If my ISP were to block any ports (i.e. 80, 443, 25565) I would be SoL, I'd either have to use an obscure port, or find some other way to traverse NAT.
(Think CGNAT, the bane of most Starlink users' existences.)
This introduces a solution that I've seen used more and more: VPN-Gateways
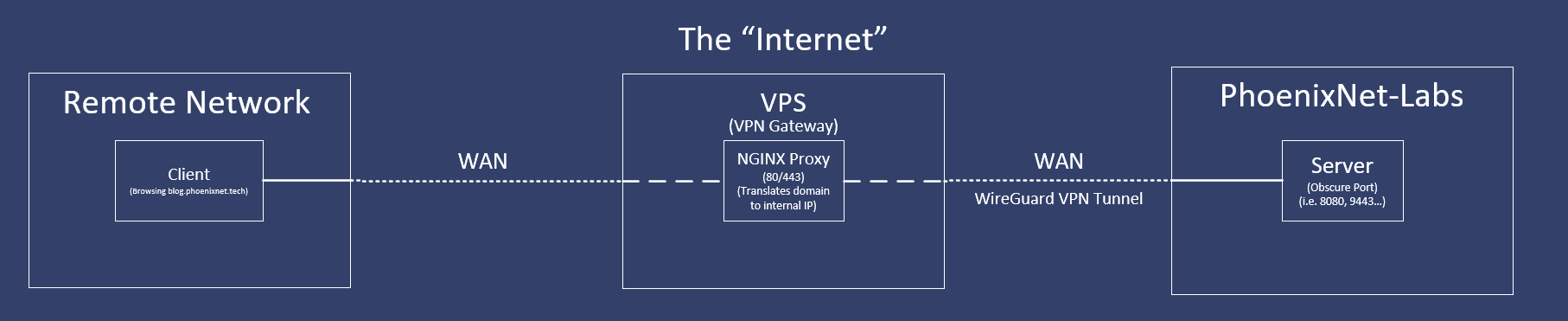
By introducing an intermediary peer (the VPS) we gain several protective features:
A) The public IP address of our intranet is now hidden behind the public IP of the VPS, which now provides a "shield" from the internet.
B) All hosted services can be shut-off with a single-click, by disabling the WireGuard VPN tunnel, the proxy will be cut-off from our server(s) inside our intranet.
Unfortunately, this introduces some delay and further complexity in network traffic flow:
- The WireGuard VPN adds ~30-100ms of latency, this is expected as it adds another layer of network traversal for traffic to travel.
- By placing the proxy server outside of the intranet, there were a few complications with particular software, but nothing that couldn't be mitigated.
Ultimately, by moving my proxy-server to outside my network, I've moved my attack vector from my internal network to my VPS.
Now, this doesn't "solve the problem" but it's a great move in the right direction!

Since moving the proxy to a VPS, my attack-logs in my IPS/IDS have gone from 50-100/daily to just 5-10/daily. What a massive difference!
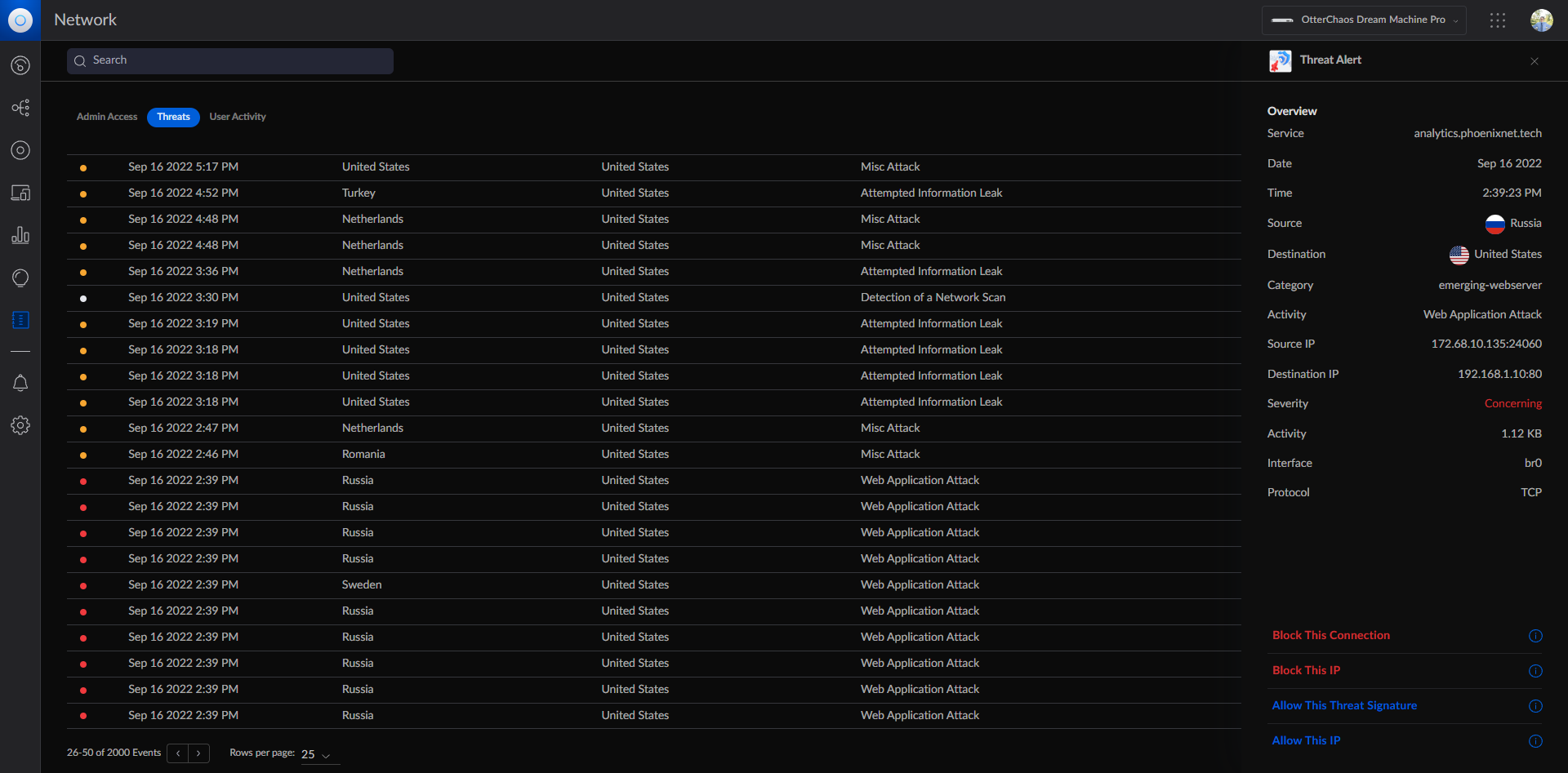
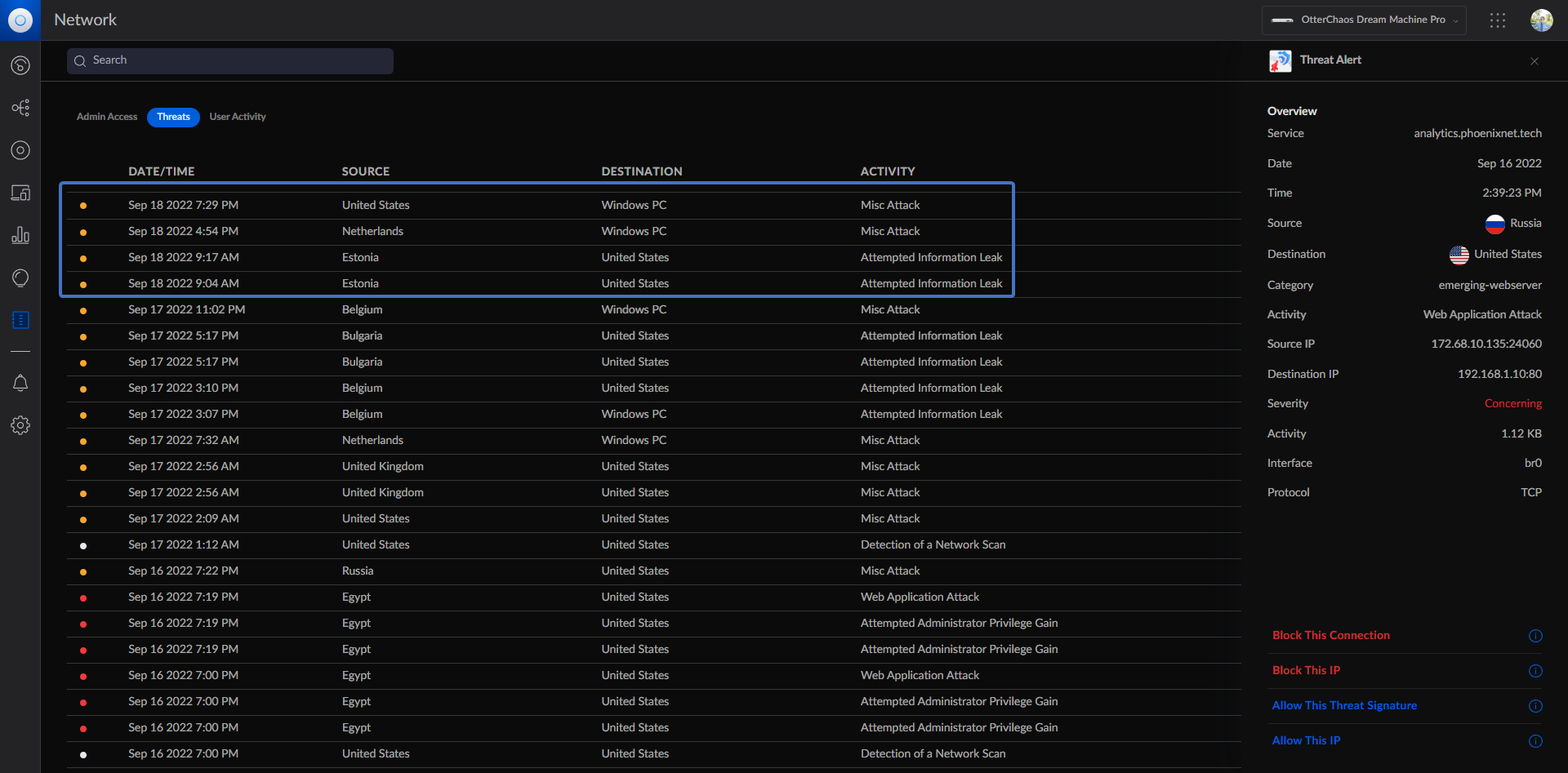
That's about it for now, but I've decided to avoid exposing my public IP / punching holes in my firewall going forward to help increase security!
I'd also like to give honorable mention to how difficult it is to setup DUO on UNIX based systems. While building the VPS (It took me 3 tries by the way, 3 RESETS.) I decided to implement DUO into the login process as well as all user elevations.
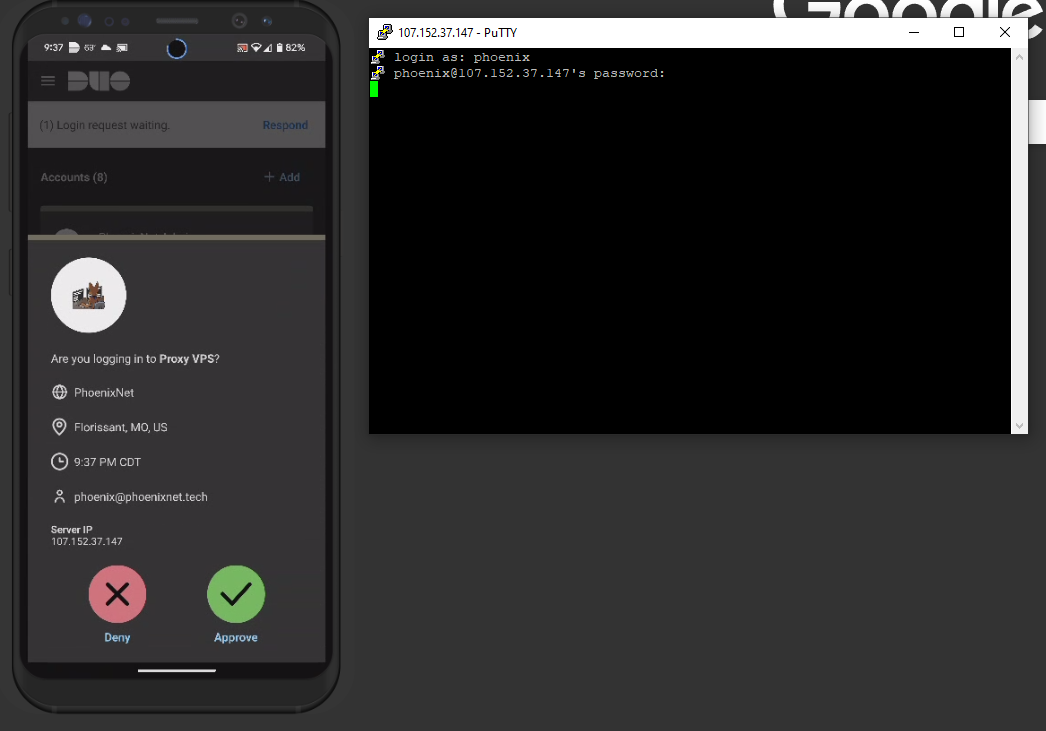
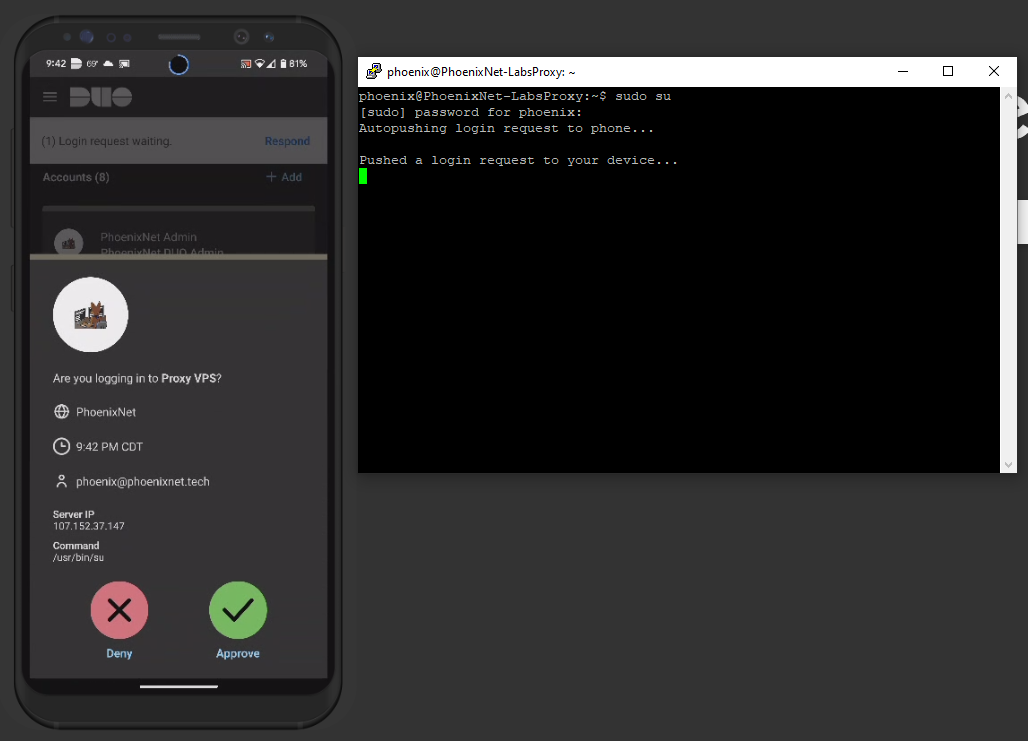
The documentation is ROCK SOLID, but it's more of a gripe regarding the tediosity of it all, a single-run script would have been more preferable. While installing and configuring, I kept locking myself out of my VPS after missing certain lines, or characters, but that's just part of the learning experience I suppose!